Dubbed by the FBI as the $26 billion scam, Business Email Compromise (BEC) attacks come with an average cost of $5.01 million per breach according to the 2021 IMB Cost of Data Breach Report. Do you have that type of capital to mitigate the costs of such a breach? If not, read our extensive blog post on BEC and how to protect your organization from such costly email attacks.
What is BEC?
Behind every great human invention, there’s an unfortunate malicious actor trying to exploit it. Your business email addresses are no different – email scams have existed since the dawn of emails and cybercriminals are always one step ahead in adapting their tactics to circumvent the existing security protocols.
BEC (also known as the man-in-the-email scam) is a scam in which financially-motivated adversaries trick unsuspecting executives and employees into making payments or sending sensitive data to fraudulent accounts. Attackers accomplish this by using a variety of social engineering tactics, that manipulate users into sending money or data.
The social engineering aspect of the Business Email Compromise attacks makes them notoriously difficult to prevent, since cybercriminals don’t rely on malware, but instead they employ elaborate impersonations to trick people into acting on the attacker’s behalf.
Types of BEC?
The FBI defines five major types of BEC scams. Let’s have a quick look at each of them:
· CEO Fraud: Malicious actors position themselves as the CEO or executive of a company and typically email an individual within the finance department, requesting funds to be transferred to an account controlled by the attacker.
· Account Compromise: In this case, an employee’s email account is hacked and is used to request payments to vendors that are wired to fraudulent bank accounts.
· False Invoice Scheme: This tactic is commonly used against foreign suppliers. The attacker impersonates a supplier and requests fund transfers to fraudulent accounts.
· Attorney Impersonation: This social engineering tactic targets mostly lower-level employees that don’t have the knowledge to question the validity of the request. In this case, the attacker impersonates a lawyer or legal representative.
· Data Theft: These types of attacks typically target HR employees in an attempt to obtain personal or sensitive information about individuals within the company such as CEOs and executives. This data can then be leveraged for future attacks such as CEO Fraud.

How Do BEC Attacks Work?
BEC scammers weaponize trust among the members of a given business by impersonating a trustworthy individual within the organization—typically a fellow colleague, manager, or vendor. The sender asks the recipient to make a wire transfer, divert payroll, change banking details for future payments, provide data, and so on.
Because BEC focus on human frailty rather than technical vulnerabilities, they require a people-centric defense that can prevent, detect, and respond to a wide range of BEC and EAC techniques.
Below, we will look into the four phases of a typical BEC attack.
Phase I: Research
The first stage of a typical BEC attack starts with careful research of the target. Attackers begin by building a targeted list of emails that are typically mined from LinkedIn profiles or business email databases. Since attacks are generally targeted at personnel authorized to make payments, cybercriminals carefully collect and assemble the various data points to produce the most successful impersonation.
Phase II: Prepare
Scammers prepare for the attack by performing activities such as spoofing email addresses or creating lookalike domains, impersonating trusted vendors, or taking over a legitimate email account of the victim’s manager or colleague.
Phase III: Execute the attack
The actual BEC attack can take place in one email or an entire thread, depending on the adversary’s thoroughness. This communication often uses persuasion, urgency, and authority to gain the victim’s trust. The perpetrator then provides wire instructions to the victim to facilitate making payments to a fraudulent account.
Phase IV: Disperse payments
If attackers can successfully build trust with an individual, this is typically the phase where financial gain or data breach is made and dispersed across different accounts or databases.
Real-Life Examples of BEC Attacks & Their Cost
Many organizations, from small businesses and major enterprises to NGOs and entire governments, have experienced BEC attacks in the past. Let’s look through some real-life examples:
1. Facebook and Google: $121m BEC scam
Considered to be one of the biggest BEC scams to date, this elaborate BEC attack resulted in $121 million in collective losses for both tech giants. The attack occurred between 2013 and 2015 and its’ perpetrator Evaldas Rimasauskas, was sentenced to five years in prison. The attack itself is a typical False Invoice Scheme – the attackers set up a sake company (Quanta Computer) that impersonated a real-life hardware supplier, then proceeded to present the two tech companies with convincing invoices and counterfeit lawyers’ letters and contracts to ensure that once the funds were paid, the bank would accept the stolen capital.
This is probably one of the most important BEC attacks to date because it teaches us a valuable lesson – if two of the world’s biggest tech companies lost millions of dollars over a two-year period, it could happen to any business. It could happen to you!
2. Toyota 2019: $37 million BEC attack
In 2019 Japan’s Toyota Boshoku Corporation was hit with a $37 million BEC attack, where hackers were able to manipulate an employee to transfer the funds out of the European subsidiary before being detected.
3. Government of Puerto Rico: $2.6 million transfer
As we talked about earlier, nobody is immune to a BEC attack and that includes the governments of nation-states. This attack could make your blood boil, because it exploited a serious tragedy – in early 2020 while dealing with the aftermath of a 6.4-magnitude earthquake, the Puerto Rican government discovered they had fallen victim to a BEC scam. The direct victim of the scam was Rubén Rivera, finance director of Puerto Rico’s Industrial Development Company who received a convincing email explaining that there had been a change to the bank account tied to remittance payments and ended up transferring over $2.6 million to a fraudulent bank account.
How to Protect Your Business from BEC Attacks?
Safeguarding your business from malicious actors and the numerous online threats is what we do at CRI Advantage. Recently, we discussed the cybersecurity do’s and don’ts and we will reiterate some of those suggestions within the context of BEC attacks.
Do enable MFA on business accounts and workflows that will significantly reduce the likelihood of accounts being compromised and used to carry out BEC attacks. Keep in mind the high-risk employees like C-level executives, employees with authority to conduct payments, HR departments, and admin accounts. With the growing popularity of remote work, it’s also essential to create your own authentication means when none exists.
Don’t rely purely on native email security, especially nowadays when more and more people are working remotely. While email providers such as Office365have significantly improved their native security, the built-in cloud security should be the base, not the entirety of your email security.
Do engage your employees with regular tests to encourage healthy skepticism and assess the levels of cybersecurity awareness. BEC attacks are tricky to prevent, exactly because they target people’s lack of skepticism towards individuals they trust. Conducting regular exercises where you sent targeted BEC-type emails to your employees will help you assess the levels of cybersecurity awareness in your company and conduct the proper training across the board.
BEC is a serious threat to any business, are you willing to take the risk? If not, book a consultation and we will review your business needs and help you identify potential cyber risks. If you aren’t ready to book a consultation, you can complete your own Cybersecurity assessment by filling out the Blueprint exercise below.
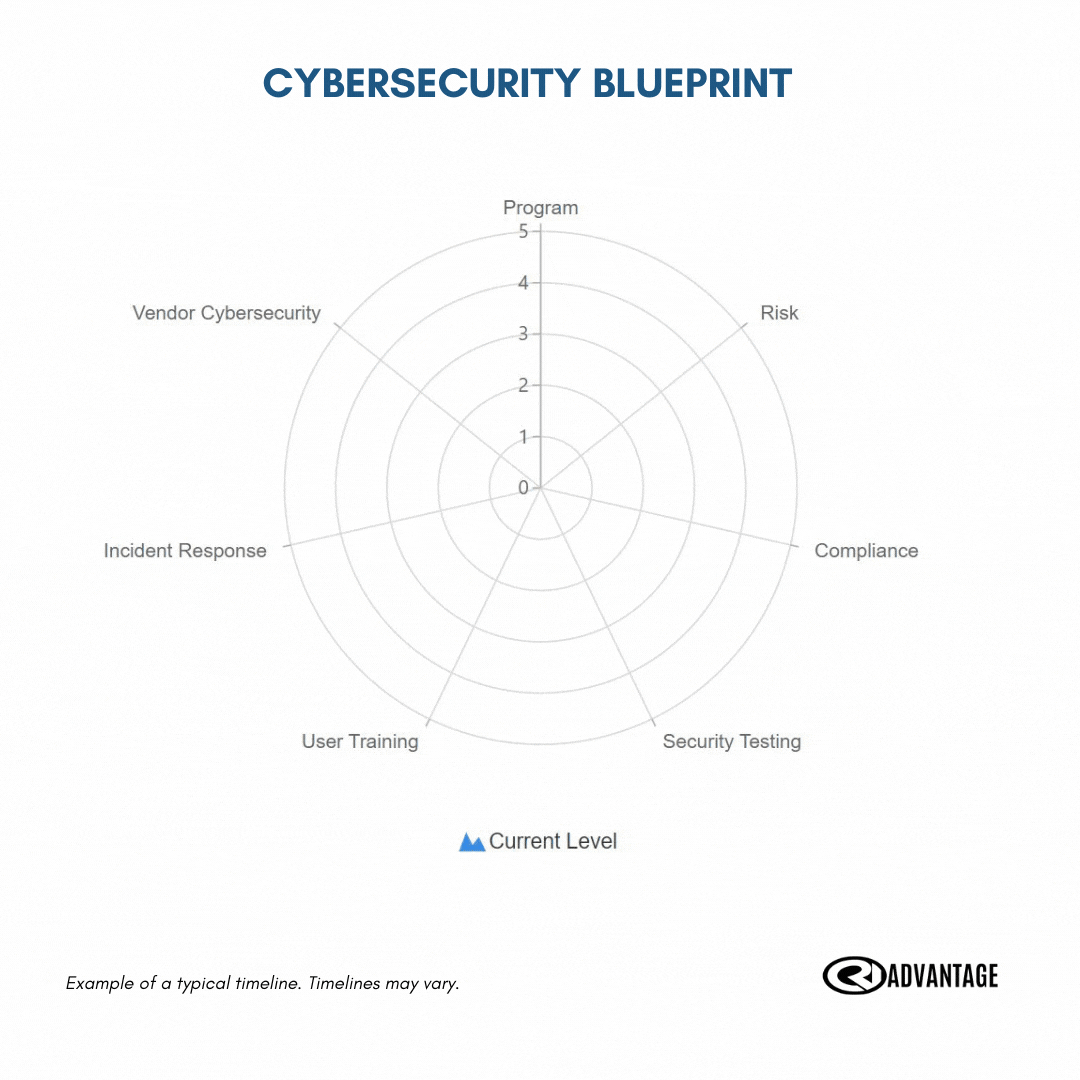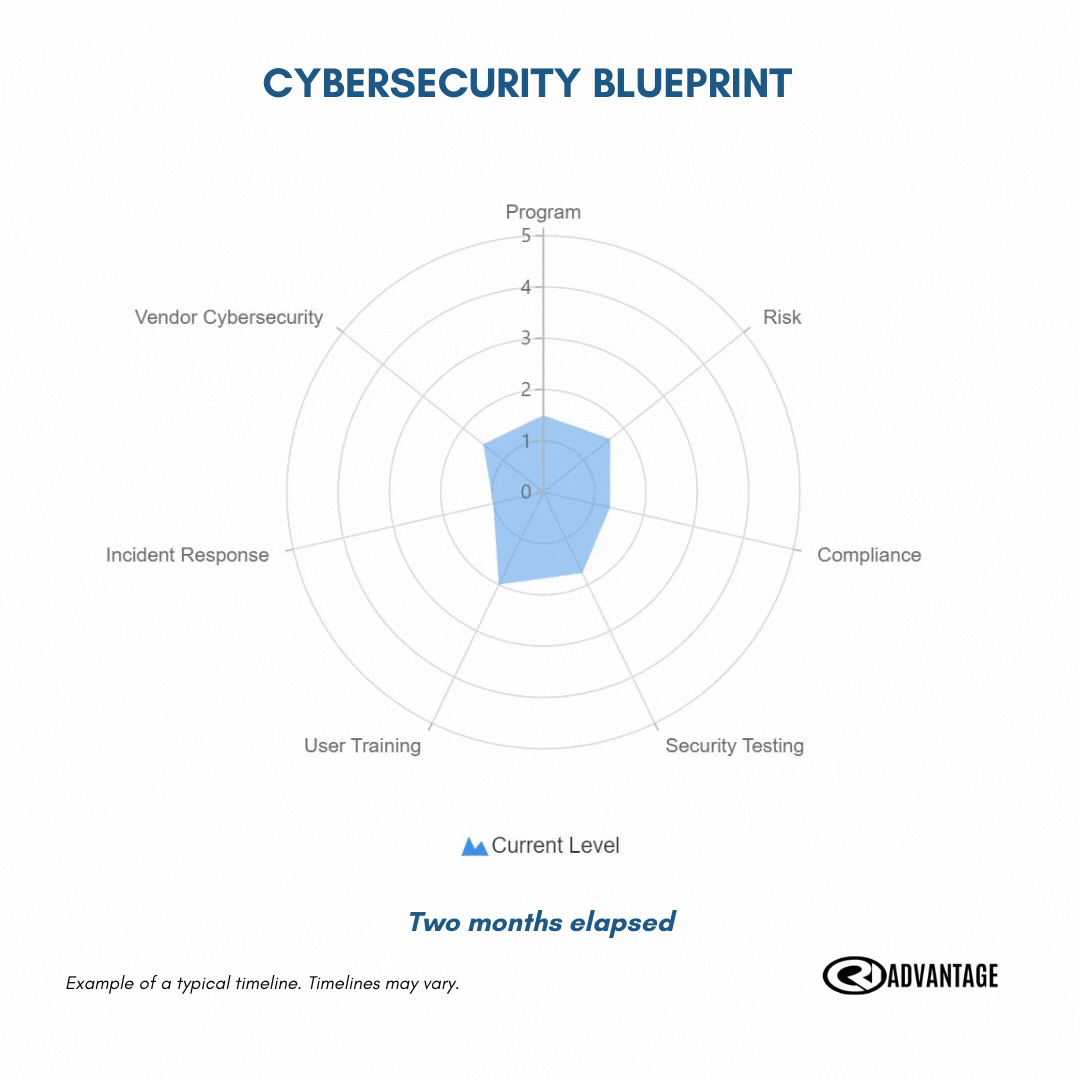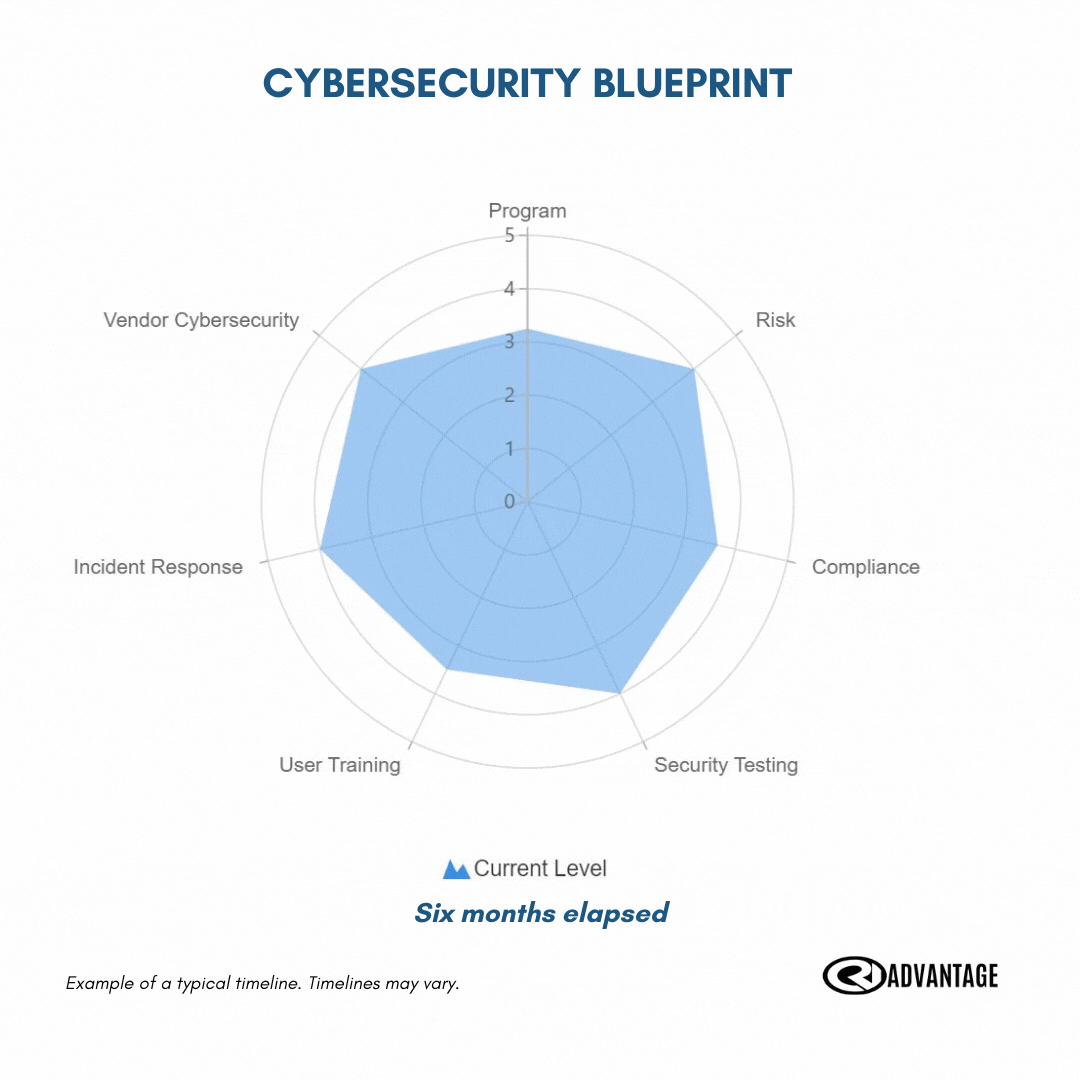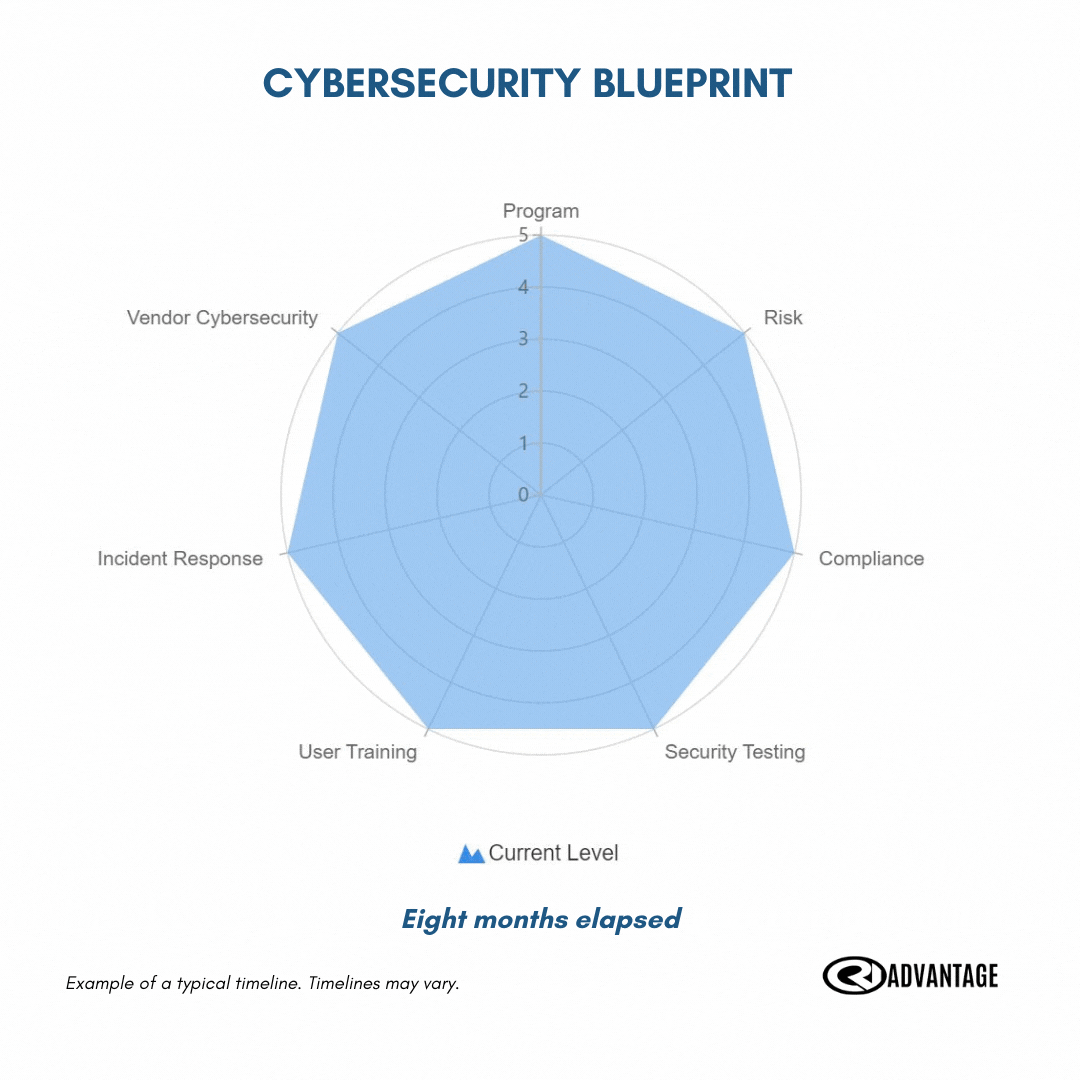
The first step: complete your cybersecurity blueprint exercise
Uncover the strengths and weaknesses of your current cyber efforts.